One major overhaul is long overdue the deployment of real-time, edge-focused AI security systems on autonomous vehicles. Original language. Founded in 2013 in Israel, Argus raised $25 million in VC funding, quickly becaming the leading automotive cybersecurity company. The automotive industry is challenged with new quality requirements due to the increasing digitalization, interaction, and automation of vehicles.  Automotive Cybersecurity. 1. Automotive refers to the securing of automotive electronic systems, communication networks, control algorithms, software, users, and underlying data from malicious attacks, damage, unauthorized access, or manipulation. It is a must to implement proper security measures in all the layers of the electronics to protect critical features and back-end networks that may become a breeding ground for cyberattacks.
Automotive Cybersecurity. 1. Automotive refers to the securing of automotive electronic systems, communication networks, control algorithms, software, users, and underlying data from malicious attacks, damage, unauthorized access, or manipulation. It is a must to implement proper security measures in all the layers of the electronics to protect critical features and back-end networks that may become a breeding ground for cyberattacks. 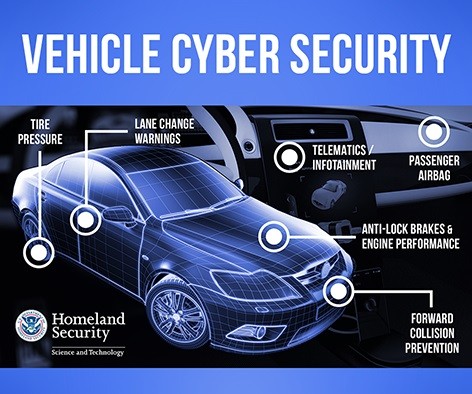 PASTA. This has a significant impact on vehicle development and the entire life cycle. Lets break down what HSMs are, how they work, and why theyre so important to public key infrastructure. This tutorial provides a set of industry standards and best practices to help manage cybersecurity risks. IT Industry.
PASTA. This has a significant impact on vehicle development and the entire life cycle. Lets break down what HSMs are, how they work, and why theyre so important to public key infrastructure. This tutorial provides a set of industry standards and best practices to help manage cybersecurity risks. IT Industry. .jpg) The list reveals that Israel is the automotive cybersecurity leader.
The list reveals that Israel is the automotive cybersecurity leader.  Welcome to the most practical cyber security course youll attend!
Welcome to the most practical cyber security course youll attend!
Global Chief of Cyber Security Services and Research Team "Software risk management is becoming ever more critical to Automotive and Industry 4.0 stakeholders. We also offer private or custom training workshops with content tailored to your specific business requirements. It introduces the basic techniques for specification, analysis, testing and proofing of security. 2.5 Protecting mobile devices from theft. This cyber security course is good for IT professionals, security professionals, and students who want to improve their knowledge about Protecting vehicle functions against unauthorized access and manipulation is a key challenge for current and future ECUs. ISO SAE 21434 Road vehicles Cybersecurity engineering focuses on cybersecurity risks in the design and development of car electronics. Learn about the evolution of the automotive industry and how its recent connection with information technology created a path towards autonomous vehicles. Overview. We strongly recommend that you have the appropriate ISO standards at hand for and during the exam, and of course during your further work. Our instructor-led automotive cybersecurity training and education are provided online or in person by UL Solutions' experts. Upstream has released four yearly reports, the latest in early 2022, on automotive cybersecurity trends with a growing amount of information.Upstream also has a public database of 900+ automotive hacking events that yield more information when Legal and regulation reinforced to establish a collective pressure to improve protection Another lever that emphasizes security in automotive is the evolution of the regulations. 2.2 Blocking unauthorized connections. Finally, we will discuss the importance of cybersecurity in significantly reducing risks. The participants would understand the connection between the threat and risk analysis, security concept, stakeholders' expectations, security specification, and verification and validation concept over the complete Vector has been working closely as a partner with vehicle manufacturers and suppliers for several years.
Cybersecurity Implementation: Automotive Industry vs. Manufacturers must implement powerful automotive cybersecurity mechanisms even more extensive than those used for IT cybersecurity. The Automotive Cyber Security: Protecting the Vehicular Network online training program includes the following courses: Evolution of Intelligent and Autonomous Vehicles. TOP CAR ACCIDENT LAWYERS TOP CAR INSURANCE TOP SOFTWARE TOOLS TOP 10 LUNG CANCER WRITE FOR US. It is a technology creating encrypted connections between a web server and a web browser. First chapter of automotive cyber security research group establishes chapter in Windsor. There are several industry guidelines, standards, and formal training courses related to automotive cybersecurity, but we are not going to cover those in this post. The Auto-ISAC stems from Presidential Decision Directive 63 (PDD-63) in 1998 on the creation of public-private sector partnerships for the protection of the U.S. critical infrastructure. 5 Cybersecurity in Automotive: How to stay ahead of cyber threats? Argus was acquired by German auto parts manufacturer Continental in 2017 for $450 million.
Automotive cyber security. The standard covers cybersecurity governance and structure, secure engineering throughout the life cycle of the vehicle and post-production security processes. This paper provides a tutorial introduction to visual servo control of robotic manipulators. Besides having greater scale and density, the internal system of a vehiclereferred to as the E/E (electrical and electronic) architectureis much more complex than that of a computer. Automotive Cybersecurity Training cybersecurity applied to automotive embedded systems is a 3-day course where participants discuss fundamentals of embedded systems and applications of cybersecurity in vehicles to illustrate unique vulnerabilities that are commonly exploited. In addition, this document provides an overview of system-level cyber security measures that can further enhance vehicle security. Training courses and snazzy certificates are great, but the best way to learn is by doing. Risk-based Cyber-Security in Practice. Fundamentals of automotive cybersecurity automotive cybersecurity such as CIA (Confidentiality, Integrity and Availability), Threat, Threat Agents/Vectors, Vulnerability, and Risk Assessment; Defense in Depth, etc. Fundamentals of automotive embedded system product design cycle, project management, design for production, V&V and O&M
----- --- Learn to HACK AUTOMOBILES with Practical & Hands-on Lessons -----[ ***** DISCOUNT CODE: "HACK-JULY" for flat @ 499/- INR / $6.55 USD *****] This is the most Comprehensive CAR HACKING Course to begin your PENETRATION TESTING Career & Research in Automobile Hacking.. Become an SME in the new & exciting field of Automotive Cybersecurity by learning the risks associated with Connected & Autonomous Vehicles (CAVs). It will cover the most popular concept of Cyber Security, such as what is Cyber Security, Cyber Security goals, types of cyber-attacks, types of cyber attackers, policies, digital signature, Cyber Security tools, security risk analysis, challenges, etc. Cybersecurity, within the context of road vehicles, is the protection of automotive electronic systems, communication networks, control algorithms, software, users, and underlying data from malicious attacks, damage, unauthorized access, or manipulation. Automotive cybersecurity is expected to nearly double in the coming decade.
This Cyber Security tutorial provides basic and advanced concepts of Cyber Security technology. For more than 40 years, LDRA has developed and driven the market for software that automates code analysis and software testing for safety-, mission-, security-, and business-critical markets. Conducting security testing for automotive software requires knowledge of industry requirements, challenges, and best practices.
To take one single example, the European General Data Protection Regulation (GDPR) will be effective in May 2018.
Overview While connected automobiles supply galore opportunities for shoppers, automakers and their suppliers have to be compelled to think about what the connected car suggests that for consumer privacy and security. Leverage our cybersecurity experience to expand your companys cyber expertise and skills. In this layer each vehicle needs to protect sensor data such as the Electronic Automotive Cybersecurity Course. APTIV. This cybersecurity tutorial provides comprehensive information and knowledge for aspirants to prioritize their careers in this IT field. You can also get more tips by going through this cybersecurity tutorial. Network security. AUTOMOBILE SECURITY / CAR PENETRATION TESTING is a very less visited Path and has a Refers to the network or system resources a cyber-security solution requires to operate. The guidance provided herein offers companies the ability to customize and quantify adjustments to their cybersecurity programs using cost-effective security controls and risk management techniques. vices, energy, and telecommunications, cyber - security has so far remained unregulated in the automotive sector but this is changing now with the upcoming UNECE WP.29 regulations on 4 UNECE, Proposal for a new UN Regulation on uniform provisions concerning the approval of vehicles with regard to cyber security and The standard covers cybersecurity governance and structure, secure engineering throughout the life cycle of the vehicle and post-production security processes. We have broken down the automotive cybersecurity market into three elements: cybersecurity hardware, cybersecurity-related software-development efforts, and cybersecurity processes and solutions. For Automotive SPICE training, however, you will Where, Layer 1 represents In-Vehicle Security or the protective sensor data. HSMs Explained. Automotive cyber security is a high-stakes endeavor, as software vulnerabilities in connected cars can threaten lives. Become an SME in the new & exciting field of Automotive Cybersecurity by learning the risks associated with Connected & Autonomous Vehicles (CAVs).
The Security Buddy Spam Protection Course explains different techniques that are used by attackers to spam users. This course will take you on a journey on how Cyber is critical for the safety of the vehicle in todays connected world. 4.3 has show the top to bottom security overview within 3 layer. Cybersecurity helps keep the data out of reach from the attackers by ensuring the integrity, confidentiality, and availability (ICA) of data. Hardware security modules are specialized computing devices designed to securely store and use cryptographic keys. Cybersecurity & Security for Safety Security (S4S) Training, Testing and Certification .
A static analysis tool helps enforce key automotive coding guidelines such as MISRA and AUTOSAR C++14 as well as assists with compliance to functional safety standards such as ISO 26262 and 3. Automotive cyber security testing is critical to detect the vulnerability of a systems architecture. Cyber security in four stages. Ethical Hacking and Penetration Testing Guide. United States is the least cyber-secure country in the world, with 1.66 attacks per computer during the previous year compared with just 0.1 attempted attacks per computer in England. A security researcher was able to hack into Nissan Leafs app NissanConnect, and thus control the climate settings, drain the cars battery, and access data from the users recent drives. This course will take you on a journey on how Cyber is critical for the safety of the vehicle in todays connected world. It is about protecting the vehicle from being taken over by an attacker. August 24, 2021. One of the most effective ways to improve automotive cybersecurity and prevent vulnerabilities today is to use a static analysis tool, such as Helix QAC or Klocwork .
Vector Consulting Services offers training classes about Automotive Cyber Security. The UK Government has spearheaded the drive for better cyber security for road vehicles, and has produced an eight-principle outline that covers all aspects of the area. Electrical System Security Committee) at the SAE (Society of Automotive Engineers) and has been widely reported as the worlds first standard on automotive cybersecurity. The aim of this document is to list and describe the main cyber security mechanisms implemented in AURIX microcontrollers, and how to use them to increase security in Automotive Electronic Control Units (ECUs). As additional connected vehicles hit the roads, computer code vulnerabilities become accessible to malicious hacker victimization cellular networks, Wi-Fi, and Cyber-attacks on vehicles have been on a steady rise since 2016. Since the topic spans many disciplines our goal is limited to providing a basic conceptual framework. 2 Cybersecurity in Automotive Industry. First, security-by-design as an engineering effort to mitigate and/or reduce the risk of an attack in progress. Until now, implementing cybersecurity systems on autonomous vehicles has largely been a one-time event. It is used to protect the information in online transactions and digital payments to maintain data privacy.
Generate effective information protection methods to increase companywide security. Automotive Cybersecurity Training cybersecurity applied to automotive embedded systems is a 3-day course where participants discuss fundamentals of embedded systems and applications of cybersecurity in vehicles to illustrate unique vulnerabilities that are commonly exploited.
Automotive refers to the securing of automotive electronic systems, communication networks, control algorithms, software, users, and underlying data from malicious attacks, damage, unauthorized access, or manipulation.
It helps to safeguard vehicles from unauthorized access to steering controls or advanced driver assistance systems (ADAS) via over-the-air updates, infotainment systems, or mobile apps.
3 How to Prevent Cyberattacks. We will review software development in the automotive world, list the most common vulnerabilities at the hackers disposal, and show proven examples of exploitation based on penetration testing of Argus Cyber Security research team.
This tutorial gives an introduction to novices in CPS and particularly highlights the basics of control theory with respect to automotive applications. Cybersecurity, Cybersecurity In Automotive / By Cybersecurity-Automation.com Team. Effective E-Learning for Employees.
For robust protection of data, and by extension the safe operations of the vehicle, a layered cyber secure approach must be taken. Demand for hardware security modules (HSMs) is booming. This is a expanding set of tutorials about Cybersecurity in the automotive sector. ISO SAE 21434 Road vehicles Cybersecurity engineering focuses on cybersecurity risks in the design and development of car electronics. Argus Cyber Security. Well check all the Cybersecurity, within the context of road vehicles, is the protection of automotive electronic systems, communication networks, control algorithms, software, users, and underlying data from malicious attacks, damage, unauthorized access, or manipulation.
Based on the terms and definitions as used in ISO/SAE 21434, this course We protect you from attacks that antivirus cant block Im Andra, and along with the Heimdal Security team, well take you on a wild ride in the universe of cyber security. 2.3 Protecting the mobile device.
Cybellum brings vital visibility into the modern software supply chain, proven vulnerability management, and extraordinary cybersecurity expertise" Automotive Cyber Security Fundamentals Automotive refers to the securing of automotive electronic systems, communication networks, control algorithms, software, users, and underlying data from malici USA USA +1 332 282 5666 usa@nobleprog.com Ask Argus Cyber Security. Aptivs self-driving cars were the first to be tested in Singapore and are slated to be fully implemented there by 2022. Below, in Fig. This is Part 1 of a three-part interview about the report Securing the Modern Vehicle: A Study of Automotive Industry Cybersecurity Practices. Continuous Cyber Security Activities (Clause 7): defines the cyber security activities need to be performed during all the phases of the product lifecycle. Cyber Security Tutorial - Before Learning Cyber Security, everyone should know system administration, C, C++. Automotive Cybersecurity Course. So if you want to get into the world of Cyber Security and Ethical Hacking, Kali Linux Installation is the first step for you. The automotive cyber security market is expected to reach USD 7.89 billion by 2028. This includes Cyber Security monitoring, Cyber Security event assessment, Vulnerability analysis, Vulnerability Management. How it's using cybersecurity in autotech: Mocana develops mobile app cybersecurity solutions for the automotive industry. Its end-to-end automotive cybersecurity system features software that allows for secure "over-the-air" and "over-the-web" firmware updates to a car's operating system.
The first concerns the individual electronic components, which act as tiny computers responsible for all manner of functions in the vehicle. Continental looks at it from four angles. Founded in 2013 in Israel, Argus raised $25 million in VC funding, quickly becaming the leading automotive cybersecurity company. 10) Explain SSL. During this interactive automotive cybersecurity course, participants will gain in-depth knowledge of various requirements for automotive cyber security standard ISO 21434. Working with clients to achieve early error identification and elimination, and full compliance with industry standards, LDRA traces requirements through static and Kali Linux is a Debian-based Linux distribution aimed at advanced Penetration Testing and Security Auditing. Our automotive cyber security training portfolio covers the fundamental concepts of digital security in vehicles including: secure system construction, hardware, software, human-computer interface, cryptography and secure interactions. In my experience, Upstream Security has the best public information on automotive cybersecurity trends. ISO/SAE 21434 presents a comprehensive cybersecurity tool that addresses all the needs and challenges at a global level. A solution with high overhead can dramatically reduce the performance of the IVN or ECU to which it is deployed. The Automotive Cybersecurity: Terms and definitions video course is one of the helpful cybersecurity awareness online courses designed to establish the basics around automotive cybersecurity (and related documents and topics): with the help of clarity on the related terminology. Overview. Thales designs, builds, and operates cybersecurity solutions to protect all critical assets and connected systems of automotive industry players.
Argus was acquired by German auto parts manufacturer Continental in 2017 for $450 million. Automotive CyberPhysical Systems: A Tutorial Introduction Abstract: This tutorial gives an introduction to novices in CPS and particularly highlights the basics of control theory with respect to automotive applications. LDRA Is Here To Help. Industry experts, David Ward and Paul Wooderson, break down the complex topic to just what you need to know to get started including a chapter dedicated to frequently asked questions.
The course also explains different anti-spam techniques that are commonly used to protect against these spams. SSL stands for Secure Sockets Layer. Automotive cybersecurity can divide the whole cyber security process in 3 layers. Search. Cyber security is one of the major tasks facing the entire automotive industry. Market Analysis and Insights of Automotive Cyber Security Market. This means that while the market is currently standing at the value of USD 1.75 billion, for the forecast period 2021-2028, the automotive cyber security market will exhibit a CAGR of 20.73%.
The security services for the automotive sector offered by the IMQ Group include the following: Architecture Threat Modeling - IMQ Minded Security can support businesses in reviewing the Architecture, evaluating the threat modelling assessment.
Auto-ISAC regularly updates a list of best practices for automotive cybersecurity which provide a risk-based approach for manufacturers, suppliers, and the The training provides an introduction to the fundamentals and practice of cyber security engineering.
Java, PHP, Perl, Ruby, Python, networking and VPN's, hardware and software. 8. Systems are designed to prevent unwanted intrusion, placed on vehicles at the time of manufacture, and then forgotten. The first step is comprehensive security testing that helps to detect vulnerabilities in a vehicles code at early stages. They prevent data theft by monitoring network connections. Cyber security in automotive is about the protection of the software running in the vehicle, as well as the communication between vehicles, smart devices, and the cloud. As an accredited body for automotive cybersecurity, we are at the forefront of national and international efforts to promote the development of ISO/SAE 21434 and keep our customers up to date on the latest developments. 2.4 Encrypted data transfer. The companys cybersecurity tools protect everything from a car's infotainment system to its wiring. It comes under the purview of the National Infrastructure Protection Plan (NIPP 2013) - Partnering for Critical Infrastructure Security and Resilience. With this tool, automotive stakeholders can perform threat analysis and risk assessment (TARA) as demanded by the WP.29 and as described in ISO/SAE 21434 standard, in Sections 8.3-8.9. This Automotive World report investigates how vehicles, organisations and data can be protected from cyber attacks. Learn the details of how you can become an Automotive Cybersecurity SME and leverage your skillset to become a leader in this new area of Cybersecurity Course Program Details. Kali Linux is the most popular OS used by Cyber Security experts all over the world. Network security refers to a set of rules and configurations to protect network traffic and data. 4.2.1 Automotive Cyber Security Layers. In the following, we would like to share our know-how with you. In 2015, researchers managed to crash a Jeep Cherokee off the road. Automotive Cybersecurity Introduction. The Understand malware, its types and case studies. With this tool, automotive stakeholders can perform threat analysis and risk assessment (TARA) as demanded by the WP.29 and as described in ISO/SAE 21434 standard, in Sections 8.3-8.9. Just like IT local area networks and endpoints, they are subject to cyberattacks . Symantec, a maker of security software, reported in 2008 that new malware released each year may outnumber new legitimate software. System Complexity. Manufacturers must implement powerful automotive cybersecurity mechanisms even more extensive than those used for IT cybersecurity. 2.1 Mobile device security is becoming more important in cars. A recent cybersecurity report identified 29 potential attack vectors among the millions of endpoints in a connected cars ecosystem. For the Cybersecurity Engineer training (TV Nord) this concerns ISO/SAE 21434, for the Functional Safety Engineer course (TV Rheinland) the safety standard ISO 26262.
The Automotive Information Sharing and Analysis Center (Auto-ISAC), formed by automakers in August 2015, is a global information-sharing community designed to address vehicle cybersecurity risks.